H-ISAC Member Observes Exploitation of Log4Shell Vulnerabilities Targeting VMware Horizon Clients
Health-ISAC Member Observes Exploitation of Log4Shell Vulnerabilities Targeting VMware Horizon Clients for Malicious Web Shells
January 5, 2022
TLP White
Health-ISAC Threat Operations Center (TOC) has received a new intelligence report from the National Health Service (NHS) regarding an unknown threat group weaponizing Log4Shell to target VMware Horizon Clients in order to install malicious web shells. Health-ISAC has released separate, initial alerts regarding Log4j, which can be accessed here and here. The NHS report's contents can be found in this alert below:
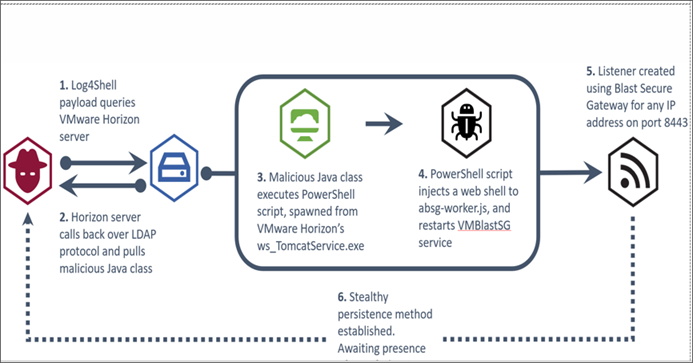
An unknown threat group has been observed targeting VMware Horizon servers running versions affected by Log4Shell vulnerabilities in order to establish persistence within affected networks. According to NHS, the attack likely consists of a reconnaissance phase, where the attacker uses
the Java Naming and Directory Interface (JNDI) via Log4Shell payloads to call back to malicious infrastructure.
Once a weakness has been identified, the attack then uses the Lightweight Directory Access Protocol (LDAP) to retrieve and execute a malicious Java class file that injects a web shell into the VM Blast Secure Gateway service. The web shell can then be used by an attacker to carry out a number of malicious activities such as deploying additional malicious software, data exfiltration, or deployment of ransomware.
The full, original NHS report can be accessed here.
A representative diagram of the attack, provided by NHS, can be accessed below:
Recommendations
Sources
|
For help with Cybersecurity and Risk Advisory Services exclusively for AHA members, contact:

