Why & How to Incorporate Cyber Risk Management Into Enterprise Risk Management
A high-level guide for hospital and health system senior leaders
By John Riggi, Senior Advisor for Cybersecurity ad Risk, American Hospital Association
Executive Summary
First and foremost cyber risk should be evaluated in terms of potential risk to patient care and safety. Security and privacy of patient data is very important but not above patient safety. Secondly, cyber risk is an enterprise risk issue – because it is present and impacts every operation and function of the organization. It is important to understand how a digital risk may translate into a physical risk to patients. For instance, a ransomware attack may render life-saving medical devices inoperable, deny access to critical health data or shut down HVAC systems and elevators which interrupt patient care operations. Cyber risk is a factor to be considered in strategic business decisions and when assessing “over the horizon” strategic risk.
This article will:
- Demonstrate why cyber risk goes far beyond an IT risk and responsibility and should be addressed in the enterprise risk management framework that encompasses patient care and safety, financial, legal, regulatory, operational, privacy, reputational and strategic risks.
- Document how organized, foreign and often state-sponsored gangs have replaced rogue hackers as the leading perpetrators of cyber crime against health care organizations.
- Explain what the differentiation between cyber risk management and enterprise risk management means for overall hospital risk management practices.
- Present examples, research and recommendations to help hospital risk management professionals better account for and integrate cyber risk within enterprise risk management programs.
For most organizations, assessing risk is fundamentally done by considering impact on the intertwined concepts of reputation, revenue, legal and regulatory exposure. For health care organizations, attitudes toward cyber risk must expand beyond the narrow view that the risk resides solely within the information technology silo and purview – that it’s an “IT” issue. This lends to the view that the primary objective of the information security function is to maintain data protection and privacy.
Perhaps the “information” security terminology itself draws attention away from the primary objective of mitigating “cyber” risk – which is to protect patients. No doubt, protecting patient data is very important, but that is secondary to protecting people. The cybersecurity function protects patients, by ensuring the availability and integrity of care operations, medical devices, health data and mission-critical systems, which all are dependent on connected technology. Think about how technology is present and weaves its way, like a fiber optic cable, through every room, hallway, system and function in a hospital. There is the specter of cyber risk wherever there is network-connected technology present, and in any function that is dependent on connected technology, either within the walls of the hospital or through its business associates.
With this premise in mind, effective cybersecurity in a hospital requires close integration and cooperation among the organization’s cybersecurity function and the staffs of all its business, operations, administrative and clinical functions. Consequently, for most hospitals and health systems cyber risk management needs to be more deeply integrated within enterprise risk management than it is today. Many hospitals struggle to effectively integrate cyber risk management within enterprise risk management, and continue to treat cybersecurity as a siloed, IT issue.
Introduction
Cyberattacks have far-reaching consequences that directly threaten patient care, patient safety and broader public health and safety, by potentially denying the availability of the hospital and emergency medical care to the community. Ransomware attacks, data theft and compromised data privacy are the best-known examples and consequences of cyber harm, but there are many more. For example, hackers have demonstrated they can remotely disable lifesaving medical devices as a result of a ransomware attack. They have forced hospitals to close or redirect ambulances by blocking access to electronic medical records and other essential systems. Cyberattacks are a clear and present danger to patient care and safety. That was already a well-accepted premise, which became even more clear when cyber attacks on health care facilities increased after the COVID-19 outbreak, despite certain ransomware gangs publicly declaring that hospitals were “off limits” during the crisis.
Just as the nature of cyber threats and their consequences have changed, so have the demographics of cyber criminals. The threat profile is evolving to include more foreign-sponsored, organized attacks. Hostile nation states such as North Korea and Iran, which are under intense financial and internal political pressure to overcome economic sanctions, have enlisted cyber criminals to raise money through cybercrime such as ransomware attacks, theft of intellectual property, bank funds and cryptocurrency. Many international cybercriminal gangs often collaborate with hostile intelligence services for mutual benefit, exchanging their hacking knowledge and capabilities which they direct toward intelligence targets, in exchange for immunity to conduct extraterritorial, lucrative cyber crimes. Almost all of these cyber adversaries are located overseas in non-cooperative foreign jurisdictions such as Russia, China, North Korea and Iran. For example, the WannaCry ransomware virus, which was the first known global ransomware attack to successfully exploit vulnerabilities in medical devices, was launched by a group of criminal hackers employed by the North Korean government. Some ransomware gangs operate in the open and even issue press releases. CLOP Ransomware, DoppelPaymer, REvil (aka Sodinokibi, Sodin), Maze, Netfilim and Netwalker have all carried out ransomware attacks against U.S health care organizations; none of them are based in the U.S.
The FBI has the lead authority for cyber crime investigation and attribution, while the Department of Homeland Security (DHS) has primary responsibility for the protection of the U.S. critical infrastructure from cyber threats. Based upon their investigations, access to classified information and collaboration across government and the private sector, the FBI and DHS are great resources to help health care organizations understand the nature of the cyber threats they face and to help defend against them. The FBI and the DHS often issue joint cyber bulletins that identify the latest cyber threats, malware signatures and adversary tactics, which help hospitals set their cyber defenses.
There is policy momentum to augment law enforcement efforts by the FBI and the DHS in a multi-pronged approach that would involve military agencies in cyber defense. It would allow military agencies to target foreign-based cyber criminals under the theory of “forward or active defense,” in essence, preemptive offensive cyber action against hackers. Many in the government, officially and unofficially, support this multi-prong, law enforcement, intelligence and military approach as a means to increase consequences for cyber criminals in instances where their attacks pose a direct threat to public health and safety. This combined use of all elements of national power would have a very substantial impact in deterring and disrupting cyber criminals that attack hospitals. This reflects the high-level thinking by policy makers on the seriousness of cyber crimes and the defenses needed to protect the country against them. In fact, it demonstrates that the U.S. government views cyber threats within the context of a strategic threat to the nation – just as hospitals should view cyber threats as an organization wide, enterprise risk issue.
Cyber Risk Is Recognized as a Public Health Threat
Cyberattacks on U.S. hospitals increased during the early stages of the COVID-19 pandemic, which highlights why cyber risk should be considered a public health and safety threat.
Even without an extraordinary public health event, system-wide cyber risk exposure was rising because of the growth in IoT devices, government requirements to demonstrate meaningful use of technology, and data sharing agreements related to value based payment models. The American Public Health Association has recognized the growing cyber risk to public health, and was joined by 80 other organizations that sent a letter to Congress in May 2019 urging a stronger and more comprehensive approach to sector security. It reads in part:
“Since sector stakeholders are focused on providing quality care and saving lives, the cyber dimension of the sector can sometimes be viewed as secondary, or not part of the professional knowledge base. With the proliferation of health information technology and cyber systems within the critical functions of the Healthcare and Public Health (HPH) sector, there is a compelling need to address and manage the risks associated with cyber threats to HPH.”
Does your organization’s approach to cybersecurity align with the current environment? This question cannot be answered solely by considering the electronic defense measures your organization has in place. IT can lead cybersecurity efforts, but cyber risk needs to be incorporated into the overall enterprise risk management framework and receive the attendant level of executive leadership support, including from the C-suite and board. A top down culture of cybersecurity is the most important defense against cyber threats.
The required approach – treating cyber risk as enterprise risk – reveals the limitations to overly relying on the information security function. IT has much more control over systems than it does over human behavior. It is the leadership of an organization, the C-Suite, which has the most influence on the behavior and culture of an organization. A top down, consistently reinforced “culture of cybersecurity” that leverages the “culture of care” already present in hospitals can be an extremely low-cost and highly effective strategy to mitigate cyber risk in hospitals. Management support is the most influential factor for employee trust in security policiesi. Staff must understand that cyber hygiene is a form of medical hygiene which helps protect patients from viruses – the electronic kind – that could negatively impact patient outcomes. This analogy may resonate well in this coronavirus-tainted world.
Hospital leaders generally do recognize the importance of safety culture and extending it to cyber security. The challenge is how to effectively convert culture into practice. Health care organizations are recognizing the need to incorporate cyber risk into enterprise risk, but are struggling to make the transition because they are unsure how to proceed. This is often because:
- Boards, CEOs, CIOs, CISOs and CxOs have different responsibilities and may not be aligned on cybersecurity.
- Non-IT leaders in hospitals may feel they lack the requisite technical skills to understand and translate cyber risk into enterprise risk. It is critical for IT leadership to help bridge this gap.
- Legacy risk management approaches may have limitations for addressing modern cyber threats.
Between 2017 and 2019 the percentage of executives with “no confidence” in their organization’s ability to understand and assess cyber risks doubled, from 9% to 18%ii. Those with no confidence in their abilities to prevent, respond to and recover from cyber threats also increased.
There are welcome signs that health care organizations are overcoming these obstacles and improving their protection against cyber attacks. Not only do most hospital leaders consistently rank cybersecurity among their three most important enterprise risk issues, 70% of U.S. hospital boards have taken the tangible step of including cybersecurity in their risk management oversight.iii
Essential Concept: Cyber Risk is Enterprise Risk
As cybersecurity threats increase, so does the urgency to elevate cyber risk management. Cyberattacks affect more than data and systems: patient safety, access to systems and facilities (and therefore public health), intellectual property and reputation are all at risk.
Where do you draw the line between what is cyber risk and enterprise risk? You can’t. So why tolerate divisions between cyber risk management and enterprise risk management?
Professional accounting and governance association COSO (Council of Sponsoring Organizations of the Treadway Commission) and Deloitte issued a statement on the danger to segregating cyber risk:
“A business-as-usual approach to cyber risk management is bound to result in catastrophic damage. Those charged with governance, from the board to the C-suite, must drive a strong tone at the top, communicate a sense of severity and urgency, and challenge the status quo of their ERM programs and cyber security awareness throughout every level of the organization. There is little to no room for error.”
The cyber-risk-is-enterprise-risk philosophy is gaining acceptance in health care and in other sectors. The idea is not new. In 2014 the National Association of Corporate Directors recommended: “Directors need to understand and approach cybersecurity as an enterprise-wide risk management issue, not just an IT issue.”
- In 2019, Deloitte reported that the percentage of all public companies that appointed tech-focused board members increased from 10% to 17% over the last six years.
- The New York Department of Financial Services created a regulatory requirement for senior management at regulated companies to be involved in cybersecurity.
- COSO reported that 49% of all boards now address cyber issues at least quarterly.
- A 2019 studyiv commissioned by enterprise insurance giant Aon recommends cyber risk be integrated into the broader risk management framework, because: “The management of cyber risk still remains largely fragmented and inconsistent across corporate functions. Risk Managers need to take a more active role in facilitating the identification and evaluation of cyber risk, collaborating across functions (Legal, IT, Security, Operations).”
These recommendations haven’t been lost on hospitals. As noted, 70% of U.S. hospital boards now include cybersecurity in their risk management oversight.
Addressing cyber risk at the enterprise level could contribute directly to reducing vulnerability if it brings alignment among various roles in the organization. Stakeholder alignment is the second-most important variable to health care cybersecurity, according to a 2018 studyv. Alignment trailed only endpoint complexity in its effect on cyber vulnerability, making it the strongest non-technical factor studied. The report notes: “As of today, policies mostly address data privacy, not data security…If, through governance, the board can create strong stakeholder alignment on the importance of cybersecurity to the organization, this will help minimize the likelihood of cyberattacks.”
What to do is clear. How to do it has proven to be more elusive.
Effectively Incorporating Cyber Risk Within Enterprise Risk Management
Cyber adversaries most often begin their attacks on health care organizations, not with a technological hack, but rather as a psychological and social engineering effort that seeks to exploit the trusting and helpful nature of most people in the field. That is precisely why organizational alignment and top-level support are essential to good cyber defense. The aforementioned studyvi on hospital cyber risk oversight summarizes the connection: “Specifically, pressure from the board of directors appears to be essential in creating substantive cyber resiliency, as research shows that hospital management support is essential for user compliance with information security policies, which in turn are written by health care IT security professionals.”
The human component of IT systems, the end users, is often the most vulnerable component and the most attacked. For evidence, just consider how many successful ransomware attacks or other cyber incidents began with someone clicking on a malware-laden email. It is widely documented in the cybersecurity community that a vast majority of all cyberattacks, potentially more than 90%, begin with a “spear phishing” email to an unsuspecting victim, according to research from security software firm Trend Micro and others. Having a culture of cybersecurity where all staff are aware of cyber risk and attentive to their responsibility to employ good cyber hygiene as they would medical hygiene to protect patients should be an enterprise-wide priority. It requires a strategy for enterprise-wide participation and implementation, plus supporting technology systems. Cybersecurity is not solely an IT responsibility, it’s an organizational, staff and vendor responsibility, and that message needs to be consistently communicated from the top.
"The cybersecurity culture of the organization – the people, are the best defense or weakest link, and the most cost effective defensive measure."
More specifically, senior leadership needs to bridge any gaps between information security and enterprise risk management efforts. In 2019, 86% of IT teams were involved in cyber risk assessment, but only 38% of corporate risk teams werevii. The risk management organization has a major role in cybersecurity at just 49% of enterprisesviii. The chief information security officer (CISO) and enterprise risk management (ERM) roles are clearly separate and can easily become misaligned.
RIMS outlined how to achieve alignment in a 2019 white paperix, excerpted here: “IT and risk management professionals both employ various tools and strategies to help them manage risk. Although the methodologies used by the two groups differ, they are generally designed to achieve similar results. By integrating these frameworks, roles and methods, IT and risk management professionals can better coordinate their efforts to address threats and create value.”
Fortunately, cyber risk management can be incorporated into leading enterprise risk management (ERM) frameworks used by hospitals today. The AHA is currently co-leading a legislatively derived task group directed to develop resources on how to incorporate cyber into enterprise risk. The current enterprise risk models being addressed include: NIST CSF, NACD and COSO, which collectively are used by many hospitals and health systems. In March 2020 NIST released Draft NISTIR 8286, Integrating Cybersecurity and Enterprise Risk Management (ERM), a reportx that promotes integrating cybersecurity within enterprise risk management. In May 2020, the U.S. Department of Health and Human Services released a report that describes cyber risk management approaches and risk calculation methodologies that health care organizations can apply, with special guidance for smaller organizations.
Questions for Assessing an Organization’s Cyber Risk-ERM Integration
The first step for individual organizations is to determine the extent cyber risk management and enterprise risk management are currently integrated. The following questions will help organizations find their baseline:
- In your organization, is cyber risk ranked as enterprise risk?
- If so, is it ranked within the top five? Top three?
- What is your top enterprise risk issue?
- How often is cybersecurity briefed to the board?
- What board committee has oversight, and how is it engaged?
- Is the cybersecurity budget measured as a percentage of the IT budget or the enterprise budget?
- Is there a methodology to quantify the strategic cyber risk profile of the organization and align cybersecurity resources and budget based upon the risk?
- Do you prioritize all strategic cyber threats and risk mitigation controls by impact to:
- Care delivery and patient safety – first and always
- Reputation
- Mission-critical operations
- Confidence of patients, staff, community and investors
- Data protection and privacy, including health records, PHI, financial and payment data and intellectual property
- Revenue
- Legal and regulatory exposure
- Mergers and acquisitions
- Strategic business risk
The discovery and discussions needed to find answers to these questions will help prepare organizations to actively integrate cyber risk within ERM.
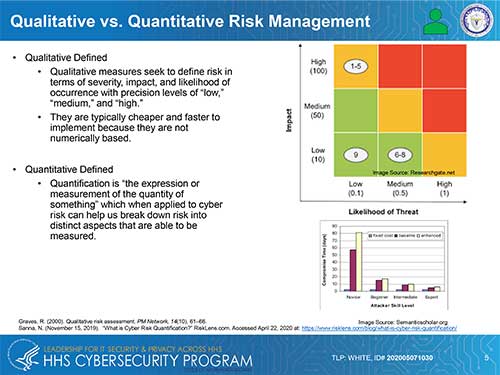
There is some specific guidance for quantifying cyber risk to hospitals and other health care organizations, and several calculation methods that are not specific to the sector are appropriate. One of the fundamental questions to resolve before calculating risk is whether a qualitative or quantitative approach should be used. HHS summarized these approaches in Figure 1 below, which was published in its May, 2020 report Quantitative Risk Management for Healthcare Cybersecurity. HHS offers a quantitative approach because it considers it more transparent, repeatable, scalable and reproducable. The qualitative approach also has its champions for cyber risk management in health care.
Quantifying Risk
FAIR, CVaR (Cyber Value at Risk), Hubbard and Seiersen (H&S) are among the methods that can be used to calculate cyber risk. There is also a simple and straightforward formula that can be applied to score specific risks so they can be prioritized:
(Threat + Vulnerability + Impact) x (Probability + Velocity) = Risk
An example of this formula being employed can be demonstrated when assessing the risks posed by a website vulnerability vs. the risk presented by Ryuk ransomware or the expiration of support for Windows. Not all threats present risk. For the threat to translate into risk, there must be a vulnerability to the threat, such as an unpatched software vulnerability. Then the organization must assess the impact to the organization, data and patient safety if a cyber attacker exploits the vulnerability. Will the impact be that a public-facing website, which is not a patient portal, goes down for a few hours, or will life-saving ventilators cease operation?
Next the organization must determine the probability of the attack. Does a patch exist which can mitigate the threat, reducing the probability and impact? Is it a widely known and targeted vulnerability such as those exploited by the WannaCry ransomware global attack, or is it a theoretical vulnerability identified by a researcher in a lab? These would all be scored differently. Next, an organization must determine the velocity of the threat exposure. How fast and where is it coming from? Is the malware that is exploiting the vulnerability currently in use and frequently targeting victims (as the Ryuk malware does), or is the threat distant, but certain, such as the set time leading up to the expiration of support for Windows 7? Even though the Windows 7 expiration has left many medical devices without security update capability, Microsoft provided months of advance notice and the option to purchase extended security updates until 2022. Once all the considerations and factors are considered organizations can determine and rank risk.
The FAIR™ (Factor Analysis of Information Risk) framework can also be used to quantify cyber risk. FAIR was developed specifically to measure cybersecurity and operational risk, and to help present it as an easily understandable enterprise risk. The FAIR Institute maintains the framework and offers many resources to help professionals learn and apply it. The H&S method is similar to FAIR in that they are both CVaR methods.
Changing the Budgeting Philosophy
Budgeting for cyber risk management as a percentage of the IT budget is a common approach. Hopefully, now you recognize it is an incomplete approach, because cyber risk is not IT specific, it is an enterprise risk. So, a hospital or health system may feel comfortable if its share of the IT budget allocated for cybersecurity falls within the 3 to 7 percent range that is common in the sector. However, that cybersecurity investment level may only represent 0.01 percent of the overall organizational budget (as we found in one consulting engagement with a hospital that had serious enterprise risk exposure introduced by cyber risk.). That level of spending clearly does not correlate to how highly hospitals rate cyber vulnerability as a risk.
Adjusting Governance for Integrated Cyber Risk & Enterprise Risk Management
While cyber risk management is best integrated within overall enterprise risk management, it still needs individual attention.
- When risk management is integrated, organizations should retain (or create) the chief information security officer (CISO) role. If the organization is not large enough to sustain a CISO, consideration should be given to designating someone who’s primary responsibility is cybersecurity.
- Ensure the CISO/cyber lead reporting structure provides sufficient status, authority and independence to be fully effective in protecting patients and the organization. The common reporting structure is for the CISO to report to the CIO. This structure works very well for most organizations, until it does not. For example, some may view the security function more akin to an IT audit function, which may represent a conflict of interest if located within the IT department. In other instances, a conflict could arise if the CIO’s priorities contradict with the CISO’s priorities or are otherwise misaligned with them. For example, when selecting new equipment, a CIO may prioritize cost savings over security features.
Once cyber risk is calculated and its integration with enterprise risk management is assessed, it is beneficial to have an independent outside expert reviewed effort. Qualified experts (which AHA can provide) can identify gaps, make recommendations and fulfill the valuable but difficult role of speaking truth to power to tell senior leaders what still needs to be done.
Summary & Conclusion
The motivations and perpetrators behind cyber attacks against health care providers have changed, and the attacks themselves have become more sophisticated and more harmful. Today, cyber risk is greater than the IT/CISO organization’s ability to protect the entire organization against it and mitigate its impact. Cyber risk is present everywhere in the organization. It is embedded in every care delivery function, technology, vendor relationship and business transaction across the enterprise. That is why cybersecurity needs to be a consistent, organization-wide effort, and why it is made more effective by instilling vigilance into the existing culture of care. Staff need to understand that cyber hygiene is as necessary as medical hygiene in protecting patients from “viruses.” One practical way to advance toward enterprise cyber risk management is to thoroughly integrate and align cyber risk management within enterprise risk management. Achieving this integration can be challenging and requires C-level and board-level support, but it can be very successful with the right understanding and right approach.
iHumaidi N, Balakrishnan V. Indirect effect of management support on users' compliance behaviour towards information security policies. Health Inf Manag. 2018 Jan;47(1):17–27. doi: 10.1177/1833358317700255.
iiMarsh, Microsoft. 2019 Global Cyber Risk Perception Survey. September 2019.
iiiMohammad S Jalali, MSc, PhD and Jessica P Kaiser, MBA. Cybersecurity in Hospitals: A Systematic, Organizational Perspective. J Med Internet Res. 2018 May; 20(5): e10059.
ivAon. Creating Value for the Cyber Risk Agenda. Cyber Captive Study 2019.
vMohammad S Jalali, MSc, PhD and Jessica P Kaiser, MBA. Cybersecurity in Hospitals: A Systematic, Organizational Perspective. J Med Internet Res. 2018 May; 20(5): e10059.
viMohammad S Jalali, MSc, PhD and Jessica P Kaiser, MBA. Cybersecurity in Hospitals: A Systematic, Organizational Perspective. J Med Internet Res. 2018 May; 20(5): e10059.
viiAon. Cyber Captive Survey 2019 Report. https://www.aon.com/captives/insights/cyber-captive-survey-2019.jsp?utm_source=Twitter&utm_medium=social&utm_campaign=AGRC&utm_term=Captives&utm_content=Cyber-captive-survey. Accessed April 24, 2020.
viiiMarsh, Microsoft. 2019 Global Cyber Risk Perception Survey. September 2019.
ixRIMS and ASACA Bridging the Digital Risk Gap – How Collaboration Between IT and Risk Management Can Enhance Value Creation. September 9, 2019.
xU.S. Department of Health and Human Services. Quantitative Risk Management for Healthcare Cybersecurity. May 2020.