Cybersecurity Advocacy Resources, Thought Leadership and Latest News
Cybersecurity vulnerabilities and intrusions pose risks for every hospital, and its reputation.
While there are significant benefits for care delivery and organizational efficiency from the expanded use of networked technology, Internet-enabled medical devices and electronic databases for clinical, financial and administrative operations, networked technology and greater connectivity also increase exposure to possible cybersecurity threats that require hospitals to evaluate and manage new risks in the context of federal privacy rules and related polices.
Hospitals can prepare and manage such risks by viewing cybersecurity not as a novel issue but rather by making it part of the hospital’s existing governance, risk management and business continuity framework.
Hospitals also will want to ensure that the approach they adopted remains flexible and resilient to address threats that are likely to be constantly evolving and multi-pronged.
Stay up-to-date on the latest cybersecurity news, resources & alerts.
Highlights
Health Industry Cybersecurity Practices: Managing Threats and Protecting Patients
Cybersecurity threats to healthcare organizations and patient safety are real. Health IT provides critical lifesaving functions. Learn more.
HHS 405(d) Aligning Health Care Industry Security Approaches
The 405(d) Program and Task Group is a collaborative effort between industry and the federal government, which aims to raise awareness, provide vetted cybersecurity practices, and move organizations towards consistency in mitigating the current most pertinent cybersecurity threats to the sector. Learn more.
Balancing Cybersecurity and Your Hospital’s Digital Transformation
Ransomware attacks and cybersecurity breaches are plaguing the health care field, jeopardizing patient data and the ability to deliver safe, efficient care. View the Transformation Talk.
Microsoft Releases Security Updates for ‘PrintNightmare’ Cybersecurity Vulnerability
Microsoft has released out-of-band security updates to address a remote code execution (RCE) vulnerability — known as PrintNightmare (CVE-2021-34527) — in the Windows Print spooler service. The Computer Emergency Response Team Coordination Center (CERT/CC), part of the Software Engineering Institute at Carnegie Mellon University, last week reported a critical RCE vulnerability impacting the Windows Print Spooler service that allows a remote authenticated attacker to execute arbitrary code with system privileges on a vulnerable system.
AHA Calls on Government to Use All Elements of National Power to Disrupt Foreign Ransomware Attackers
The Federal Bureau of Investigation May 20 issued an alert regarding “Conti,” a highly disruptive ransomware variant. Attacks associated with Conti and the previously published Darkside ransomware variant are believed to be emanating from criminal networks operating from a non-cooperative foreign jurisdiction. Ransomware attacks associated with these variants have resulted in regionally disruptive impacts to critical infrastructure, including hospitals and health systems in the United States and Ireland. These ransomware attacks have delayed or disrupted the delivery of patient care and pose significant potential risks to patient safety and the communities that rely on hospitals’ availability.
AHA Senate Testimony On Cyber Threats to Hospitals – Attacks Up, Victim Hospitals Need Government Assistance Not Blame
Within the context of the COVID-19 pandemic, in Senate testimony John Riggi discusses increased incidences of cyber threats toward hospitals and health systems, the resulting, unique challenges confronting the health care sector, and what the federal government can and must do to help ensure appropriate mechanisms are in place to share threat information and defend the nation’s hospitals and health systems from cyber attacks.
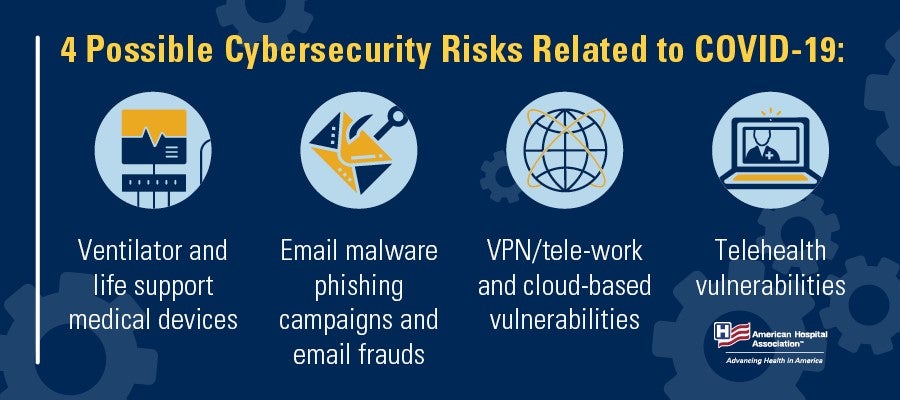
Four Ways to Mitigate COVID-19 Cyber Risks
As the nation’s hospitals and health systems, physicians, caregivers and staff treat and care for patients and our communities, there are others in the world seeking to exploit the COVID-19 pandemic for financial gain. Particularly, cyber criminals. View more.
Why & How to Incorporate Cyber Risk Management Into Enterprise Risk Management
Ransomware attacks on hospitals are not white collar crimes, they are threat-to-life crimes because they directly threaten a hospital’s ability to provide patient care, which puts patient safety at risk. That development was reinforced during the early days of the COVID-19 outbreak, when phishing emails and other cyber attacks on hospitals increased because cyber criminals treated the pandemic as an opportunity to exploit, victimize and profit. View more.
Ransomware Attacks on Hospitals Have Changed
Ransomware attacks on hospitals are not white collar crimes, they are threat-to-life crimes because they directly threaten a hospital’s ability to provide patient care, which puts patient safety at risk. That development was reinforced during the early days of the COVID-19 outbreak, when phishing emails and other cyber attacks on hospitals increased because cyber criminals treated the pandemic as an opportunity to exploit, victimize and profit. View more.
Advisory: Further TTPs Associated with SVR Cyber Actors
This report provides further details of Tactics, Techniques and Procedures (TTPs) associated with SVR cyber actors. SVR cyber actors are known and tracked in open source as APT29, Cozy Bear, and the Dukes. UK and US governments recently attributed SVR’s responsibility for a series of cyber-attacks, including the compromise of SolarWinds and the targeting of COVID-19 vaccine developers. Alongside this attribution, the United States’ National Security Agency (NSA), Federal Bureau of Investigation (FBI), and Cybersecurity and Infrastructure Security Agency (CISA) released an advisory detailing the exploits most recently used by the group. The FBI, Department of Homeland Security (DHS) and CISA also issued a joint report providing information on the SVR’s cyber tools, targets, techniques, and capabilities. Download the PDF.
White Paper: Strategic Threat Intelligence: Preparing for the Next “Solarwinds” Event
As the impact of the SolarWinds incident is still being investigated and discussed, the American Hospital Association (AHA) and Health-ISAC collaborated on this strategic intelligence analysis to identify what other “SolarWinds” like issues might be lurking in enterprise networks. The paper is meant for all audiences, non-technical and technical, as we present strategic level decision elements that senior leaders including C-Suite Executives can use to help understand the risks involved with certain enterprise IT systems in their network environment. We then provide detailed technical analysis and recommendations for IT and information security teams to help address immediate concerns by providing tactical mitigations and recommendations. For our technical audience, this paper presents a detailed analysis of characteristics that allowed the SolarWinds incident to affect multiple industries, organizations, and systems. Download the PDF.
Hackers Target on Premises Microsoft Exchange Server Vulnerabilities
Cyber attackers are using Microsoft Exchange Server vulnerabilities to access Exchange server email accounts on an organization’s premises and install malware to facilitate long-term access to victim environments, View Microsoft's announcement..
Joint Cybersecurity Advisory: Ransomware Activity Targeting the Healthcare and Public Health Sector
This advisory describes the tactics, techniques, and procedures (TTPs) used by cybercriminals against targets in the Healthcare and Public Health Sector (HPH) to infect systems with Ryuk ransomware for financial gain. Download the PDF.
The Importance of Cybersecurity in Protecting Patient Safety
Health care organizations continually face evolving cyberthreats that can put patient safety at risk. That’s why I advise hospital C-suite and other senior leaders not to view cybersecurity as a purely technical issue falling solely under the domain of their IT departments View more.
Theft of Intellectual Property: Threats to Medical Research and Innovation
There is growing concern among the Federal Bureau of Investigation (FBI), Congress and some leaders in the health sector about the threat of theft of U.S. intellectual property (IP) by foreign governments. View more.
Additional Key Cybersecurity Resources
- COVID-19: Physicians Home and Office Cybersecurity Guide
- DHS Protecting Critical Networks from COVID-19 Cyberthreats
- A Conversation with the DHS About COVID-19 Cyberthreats [Part 2]
- A Conversation with the FBI on Mitigating COVID-19 Cyber Threats
- Cybersecurity and Risk Advisory Services
- What’s Your Cyber Risk Profile?
- HC3 Sector Notice TLP White: Exploitation of SolarWinds Software Affecting HPH Sector
- HC3 Sector Alert TLP White: Active Exploitation of SolarWinds Software Potentially Affecting HPH Sector
- Russian State-Sponsored Actors Exploiting Vulnerability in VMware® Workspace ONE Access Using Compromised Credentials
- Hospital Robocall Protection Group Adopts Best Practices Report on Preventing Unlawful Calls
- Hospital Robocall Protection Group (HRPG) Report December 14, 2020
- Hospital Robocall Protection Group Virtual Meeting Agenda, December 14, 2020
- Joint Cybersecurity Advisory TLP White: North Korean Advanced Persistent Threat Focus: Kimsuky, October 27, 2020
- HC3 Threat Brief TLP White: COVID-19 Cyber Threats (Update), (August 13, 2020)
- FBI Cybersecurity Advisory TLP White: Russian GRU 85th GTsSS Deploys Previously Undisclosed Drovorub Malware, August 2020
- Current Malware Threats Targeting the Healthcare And Public Health (HPH) Sector, June 16, 2020
- FBI & CISA PSA: People’s Republic of China (PRC) Targeting of COVID-19 Research Organizations, May 13, 2020
- Joint Activity Alert: Top 10 Routinely Exploited Vulnerabilities, May 13, 2020
- CISA Insights COVID-19 Disinformation Activity, May 8, 2020
- HC3 Cyber Alert TLP White: Quantitative Risk Management for Healthcare Cybersecurity, May 7, 2020
- CISA: Guidance for Securing Video Conferencing, May 1, 2020
- CISA: Telework Guidance and Resources, May 1, 2020
- Health Industry Cybersecurity Information Sharing Best Practices - March 2020
- Draft: Data Integrity Identifying and Protecting Assets Against Ransomware and Other Destructive Events - January 2020
- The 405(d) Post Vol 3 - January, 2020
- The 405(d) Post Vol 2- November, 2019
- Members-Only: Theft of Intellectual Property: Threats to Medical Research and Innovation
- Members-Only Cybersecurity Alerts and Resources

For help with Cybersecurity and Risk Advisory Services exclusively for AHA members, contact:
John Riggi
National Advisor for Cybersecurity and Risk, AHA
(E) jriggi@aha.org
(O) +1 202 626 2272